Creating Self Signed Certificates for your Firewalls
First you need to generate a certificate signing request on your firewall. Go to System -> Certificates -> Generate and fill in the appropriate information. For example:
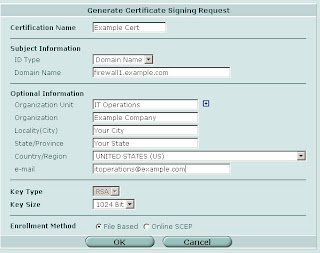
Click OK. On the next screen download the certificate request you just created.
Now you have a couple of options. You can either pay a public root Certificate Authority such as GoDaddy or Verisign to sign your certificate. They can also provide you with information on how to submit your request.
Another option is to create your own Certificate Authority using free software. In this scenario I am using XCA, a great graphical front end for the somewhat complex procedure of creating a CA and signing certificates.
- Download XCA from http://sourceforge.net/projects/xca and install it
- In XCA create a new Certificate Database: File -> New Database
- Assign a complex pass phrase to the database
Create a Root Certificate Authority in XCA
- Certificates Tab -> New Certificate and fill in your information (example screenshots below)
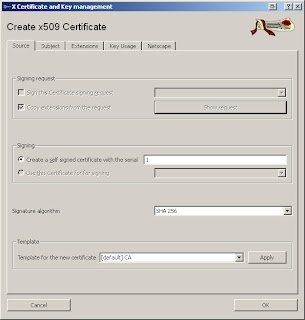
In the "Template for the new certificate" select "[default] CA" and click Apply.
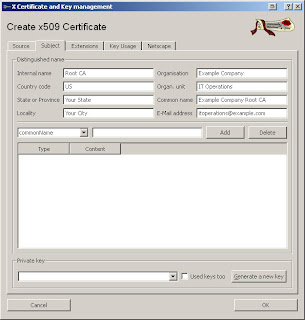
Click "Generate a new key", fill in the name and then click "Create".
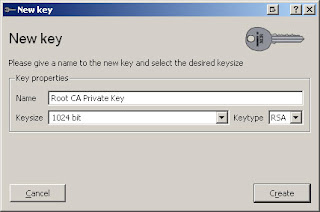
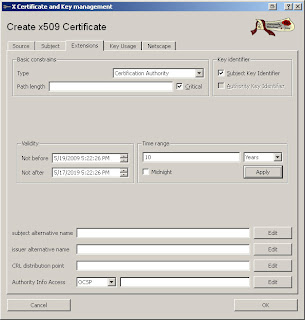
Click OK. You now have a Root CA with public and private keys.
Sign the Certificate Signing Request
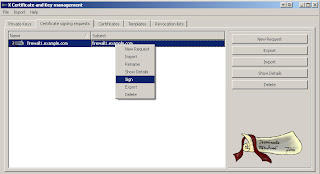
Click the "Certificate Signing Requests" tab, then "Import" and load the CSR you downloaded from the firewall. When loaded you can select the CSR and click "Show Details" to validate the information in the request.
Now right click on the CSR and select "Sign". Set your options according to the next screenshots.
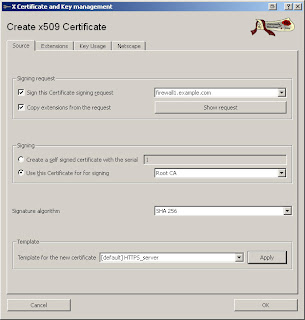
After setting the "Template for new certificate" to "[default] HTTPS_Server" click Apply. By default the certificate will be valid for 1 year from date of issue. If you need this to be valid for longer you can adjust it in the "Extensions" tab in the "Validity" section. Please note that your end device certificates cannot be valid longer than the Root CA which by default is 10 years.
Click OK.
On the "Certificates" tab expand the Root CA and select the firewall certificate. Then click "Export" and save the file using PEM as the Export Format.
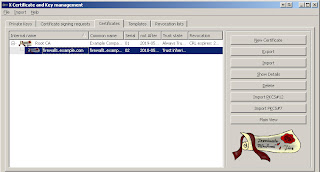 Back at your firewall return to System -> Certificates and click "Import". Select the certificate (*.crt) that you exported from XCA and click OK. The certificate is now ready for use in your firewall.
Back at your firewall return to System -> Certificates and click "Import". Select the certificate (*.crt) that you exported from XCA and click OK. The certificate is now ready for use in your firewall.

No comments:
Post a Comment